Why choose IPsec VPNs over SSL/TLS VPNs?
Publié le 07/12/2021
Author : Arnaud Dufournet, Chief Marketing Officer
Customers often wonder why they should choose IPsec VPNs over SSL/TLS VPNs. While the latter are the most widespread, both technologies provide mechanisms that ensure confidentiality, integrity, and authentication. To properly answer the question and guarantee the best possible data protection, it is essential to understand the differences between the two protocols.
A major difference that changes everything!
Let’s start with a brief historical recap. Secure Socket Layer (SSL) and Transport Layer Security (TLS) are two cryptographic protocols that enable both authentication and encryption of data transfers between servers, connected devices, and networked applications (especially when a client connects to a server over HTTPS). SSL came before TLS. New versions of these protocols followed in succession to deal with vulnerabilities and strengthen encryption algorithms for greater security. Netscape developed version 1.0 of SSL in 1994, but it never saw the light of day. It then released version 2.0 in 1995. As several vulnerabilities were discovered in 1996, SSL version 3.0 quickly replaced version 2.0. TLS 1.0 was launched in January 1999 as the new version of SSL, based on SSL 3.0. Today, TLS is considered safer than the SSL protocol, since version 2.0 has known security vulnerabilities.
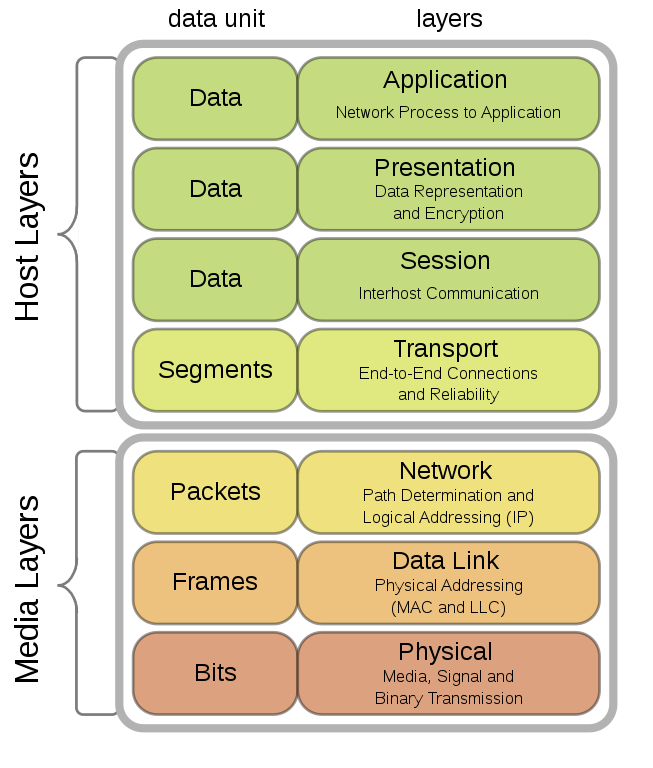
Turning to Internet Protocol Security (IPsec), it was standardized in 1995 by the Internet Engineering Task Force (IETF), the body that develops and promotes internet standards, among which the standards that are part of the internet protocol suite (TCP/IP).
IPsec brings together a number of secure communication protocols designed to protect network flows and, more specifically, to establish a private communication (a tunnel) between devices that are separated by a network deemed to be non-secure or public, like the internet.
The major difference between IPsec and SSL/TLS lies in the network layers where the authentication and encryption steps are performed. IPsec guarantees the confidentiality and integrity of a flow, by encapsulating it within the network layer (“internet” layer in the TCP/IP stack or “network” layer in the OSI model). SSL/TLS comes in at a much higher level in the network stack, placing itself on top of the TCP transport layer. The protocol is designed to ensure security over the internet by providing a “secure socket” that protects IP packets between a browser and a web server when HTTP data streams need to be encrypted.
Security level: advantage to IPsec
Now that we have explained this major difference, what are the practical consequences when it comes to deploying IPsec or SSL/TLS VPNs?
First and foremost, an IPsec VPN client requires software and hardware compatibility at both ends of the tunnel. Some of our customers have, for example, reported issues with mounting IPsec tunnels on the FreeBox, a French internet provider box. As they were originally focused on mobility, the main purpose of SSL VPNs is to protect web traffic. Because they are considered to be easier to deploy, companies who wanted to protect the connections of their teleworkers made massive use of SSL VPNs during the pandemic.
However, if you are looking for a high level of security, you will be better off turning to an IPsec VPN, as the French National Cybersecurity Agency (ANSSI) has recommended for several years now. Already back in 2015, it published Recommendations for securing networks with IPsec. In its recommendations on nomadic work practices published in October 2018, the ANSSI advocates “using the IPsec protocol rather than TLS to implement a VPN tunnel between access devices and a VPN termination device”. The reasons it puts forward are as follows:
- IPsec has a smaller attack surface*. IPsec’s critical security tasks (such as functions that use keys) are performed in a siloed environment within the operating system kernel, while TLS typically runs in the user space from the application layer.
- Mechanisms for an initial choice of algorithms* between the client and the server are more robust in IPsec than in TLS.
- Default support for authorized certificate authorities* is more permissive in the various TLS implementations than in IPsec implementations.
- Most of the recent vulnerabilities concern implementations of the SSL and TLS protocols* (POODLE, BEAST, CRIME, FREAK, Heartbleed, etc.).
The reality of these threats was immediately visible in 2020 with the massive deployment of SSL VPNs to meet the challenge of telecommuting. Three vulnerabilities inherent in this type of VPN are among the Top 10 most significant vulnerabilities of 2020 revealed in February 2021. And these weaknesses continue to be exploited in 2021. In September, we learned that nearly 500,000 FortiGate SSL-VPN login credentials were disclosed on a hacker forum.
Recommended by the NSA and the CISA
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) in their turn recommended IPsec VPNs. At the end of September, the two US agencies jointly released an information sheet on cybersecurity. Entitled “Selecting and Hardening Remote Access VPN Solutions“, the guide defines the recommendations that organizations and businesses should follow when choosing a VPN to secure remote access to their systems. It also notes that VPNs are interesting targets for hackers to infiltrate networks. The vulnerabilities some of them offer include the ability to conduct Advanced Persistent Threat (APT) attacks. The guide also lists the consequences of malicious actors exploiting common vulnerabilities:
- Credential harvesting
- Remote code execution of arbitrary code
- Cryptographic weakening of encrypted traffic sessions
- Hijacking of encrypted traffic sessions
- Arbitrary reads of sensitive data
The guide provides advice on choosing your VPN to protect yourself in the best possible way against risks. More specifically, it recommends selecting vendors that are known to quickly address vulnerabilities as they are revealed and who follow best practices in terms of authentication. It also lists key features that are must-haves and that you need to configure before you implement a device:
- Test the VPN before you deploy it
- Use the IKE/IPsec protocol and not SSL/TLS
- Use multi-factor authentication (MFA)
- Reduce additional VPN features to the bare minimum to reduce the attack surface
- Protect and monitor access from and to the VPN
TheGreenBow has long offered a full range of IPsec VPN clients that follow the recommendations of the ANSSI and the National Institute of Standards and Technology (NIST), and which meet the requirements of major organizations, critical market operators, providers of essential services, and public administration bodies. Our Windows and Linux VPN Clients include many features that administrators can enable or disable according to requirements prescribed by their Chief Information Security Officer (CISO), and which are MFA-compatible, since our products provide support for tokens and smart cards. The filtering mode in our Windows Client, which allows you to protect and monitor access to and from the VPN, is another example of the recommendations that our products follow. Regardless of the operating system you use, you can test our VPN clients in order to verify that they seamlessly integrate with your security architecture.
* Source: Recommendations on digital nomadism, ANSSI guide published in 2018 (only available in French)