Migration to quantum-resistant cryptography
Publié le 25/8/2023
Guest author: Indré Vaicekavičiūtė, CyberNews
Cryptography holds a key role in maintaining data confidentiality in information security. This technique revolves around generating and deciphering codes that permit access to the data solely by approved entities. However, the emergence of quantum computing threatens to render traditional cryptographic methods obsolete, thereby creating a significant risk to the security of information.
In response to this emerging issue, professionals and coders are beginning to create encryption that is resistant to the computational capabilities of quantum computers. The development of this type of encryption is crucial to stay on top of technological progress and guarantee the protection of information.
What Is Quantum-Proof Encryption and Why Is It Important?
Quantum-resistant encryption is an advanced collection of algorithms resistant to highly advanced quantum computing systems. These encryption strategies are expected to replace conventional algorithms that use public key encryption.
In 1994, the mathematician Peter Shor brought forth the idea of quantum computers, which promised greater capabilities than existing computers. However, they were purely theoretical at that point. Fast-forwarding to the present day, there have been considerable advancements in computing technology, and quantum computers are anticipated to become a reality within the next ten years.
This progress brings about significant concerns. Existing encryption methods may not hold up against the widespread use of quantum computers. In response to this pressing issue, researchers are focusing on the development of post-quantum cryptography.
By adopting quantum-resistant encryption, we can safeguard confidential information despite technological progression. It’s essential to stay proactive and shield our data from potential future threats.
Developing a Quantum-Resistant Encryption Standard
In 2016, the National Institute of Standards and Technology (NIST) launched a competition to find a post-quantum encryption standard capable of withstanding quantum computers.
Unlike traditional encryption systems that rely on complex mathematical solutions, NIST has recently announced the shortlisting of four encryption algorithms that it deems “quantum-proof” in 2022.
These include the CRYSTALS-Kyber algorithm, the CRYSTALS-Dilithium algorithm, FALCON, and SPHINCS+.
- The CRYSTALS-Kyber algorithm, in particular, is gaining popularity as a general encryption standard due to its smaller encryption keys, facilitating rapid exchange. It also boasts impressive speed compared to other options.
- For digital signatures, the NIST officially recommends CRYSTALS-Dilithium, with FALCON serving as an alternative for cases where Dilithium may not be suitable. Both algorithms are recognized for their speed and rely on structured lattice math problems for data encryption.
- On the other hand, the fourth algorithm, SPHINCS+, may be slower than the rest, but it is considered quantum-proof due to its reliance on a distinct set of mathematical problems. Instead of structured lattices, this algorithm places its trust in hash functions.
Migration To Quantum-Resistant Cryptography
With the rise of quantum computing, traditional encryption methods are becoming increasingly vulnerable to attack. As a result, organizations must prepare for a transition to quantum-resistant cryptography in order to maintain the security of their data. This migration to new cryptosystems will require a carefully crafted strategy, encompassing everything from identifying key areas of vulnerability to selecting the most effective cryptographic algorithms.
Here is the strategy we recommend:
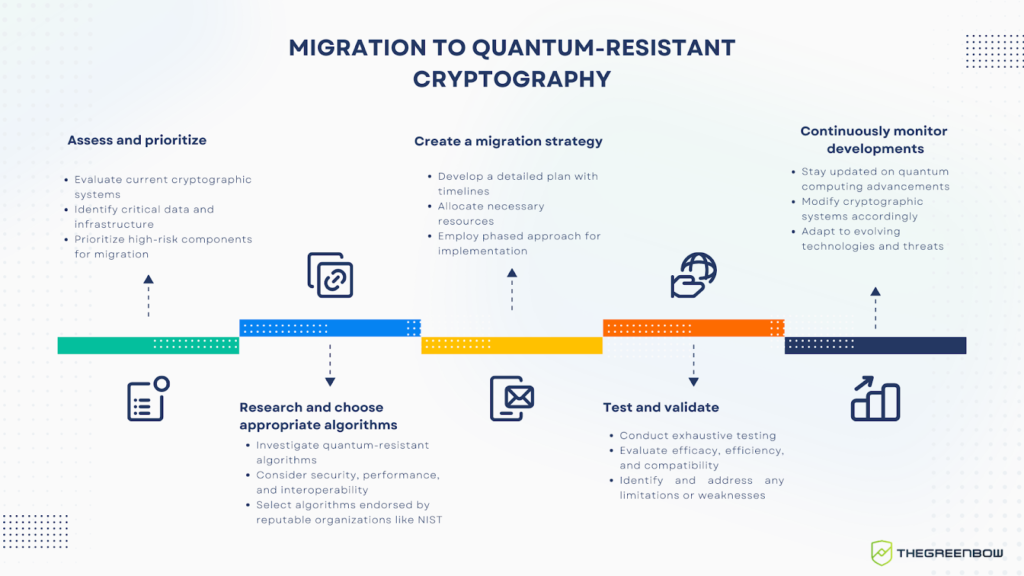
Assess and prioritize
Begin by thoroughly evaluating your organization’s current cryptographic systems, identifying the most crucial data and critical infrastructure. Prioritize migrating these high-risk components to quantum-resistant cryptography.
Research and choose appropriate algorithms
Investigate the available quantum-resistant algorithms, considering their security, performance, and interoperability. As such, it is recommended to select quantum-resistant algorithms endorsed by reputable organizations like the National Institute of Standards and Technology (NIST).
Create a migration strategy
Develop a detailed plan for transitioning, including timelines, resource allocation, and integration techniques. Consider a phased approach, starting with the most important components and gradually expanding the implementation.
Test and validate
Before deploying quantum-resistant cryptography on a large scale, conduct exhaustive testing to ensure its efficacy, efficiency, and compatibility with existing systems. Moreover, thorough testing also helps to identify any potential limitations or weaknesses of the new cryptography, allowing for any necessary refinements or improvements to be made before deployment.
Continuously monitor developments
Maintain current knowledge of progress in quantum computing and quantum-proof cryptography. Thus, it’s crucial to stay informed about technological developments in quantum computing and modify cryptographic systems as necessary.
In addition to implementing quantum-resistant cryptography, deploying a robust antivirus solution and trustworthy VPN contributes to strengthening your organization’s overall security posture during the migration to quantum-resistant cryptography. By integrating antivirus and VPN measures into your cryptographic strategy, you can further mitigate the risk of data breaches and unauthorized access.
Challenges and Pitfalls in the Migration Process
Migrating can be an extremely complex and challenging process. It is important to be aware of potential pitfalls along the way in order to successfully navigate this process. The following are some of the challenges associated with migration:
- Integration difficulties: Adapting quantum-resistant cryptography into existing infrastructures, especially in hybrid environments with diverse systems and platforms, can be challenging.
- Resource impact: Quantum-resistant algorithms often require larger key sizes and additional computational resources, potentially affecting system performance and scalability.
- Skill and expertise: Transitioning to quantum-resistant cryptography demands specialized knowledge and expertise, which may be lacking within your organization.
- Financial investment: Transitioning to quantum-resistant cryptography may require significant monetary and human resource investments.
- Price of inaction: Failure to implement quantum-resistant cryptography exposes organizations to future decryption of sensitive data by quantum computers, leading to data breaches and intellectual property loss.
- Financial losses: Inadequate cryptographic protection can result in substantial financial losses, such as regulatory penalties, legal fees, and consumer compensation.
- Reputational damage: Neglecting quantum-resistant cryptography can harm consumer confidence and reputation, as organizations may be perceived as neglecting their cybersecurity responsibilities.
- Competitive disadvantage: Organizations that delay the transition risk falling behind competitors who showcase their dedication to data security through the early adoption of quantum-resistant cryptography, earning consumer trust.
Conclusion
The shift to quantum-proof cryptography is essential for enterprises to protect their confidential data from the impending risk of quantum-powered breaches. To effectively manage this change, organizations need to grasp the challenges involved and employ a strategic method while foreseeing possible risks.
The potential damages from not integrating quantum-proof cryptography considerably surpass any preliminary investment needed for the switch. It’s vital to commence planning and instigating the transfer of your organization’s digital assets to quantum-proof cryptography promptly, guaranteeing their security in the long run.
About the author:
“Indrė Vaicekavičiūtė is an accomplished SEO Specialist and Content Manager at CyberNews. She is responsible for optimizing website content and enhancing its visibility in search engine rankings. With expertise in cyber security, SEO, and content creation, she is a renowned author, providing readers with insightful and accessible perspectives on the ever-changing landscape of digital threats and protective measures.”
